CakePHP is an open source MVC framework. It makes developing, deploying and maintaining applications much easier. CakePHP has number of libraries to reduce the overload of most common tasks. Following are the advantages of using CakePHP.
- Open Source
- MVC Framework
- Templating Engine
- Caching Operations
- Search Engine Friendly URLs
- Easy CRUD (Create, Read, Update, Delete) Database Interactions.
- Libraries and Helpers
- Built-in Validation
- Localization
- Email, Cookie, Security, Session, and Request Handling Components
- View Helpers for AJAX, JavaScript, HTML Forms and More
CakePHP Request Cycle
The following illustration describes how a Request Lifecycle works −
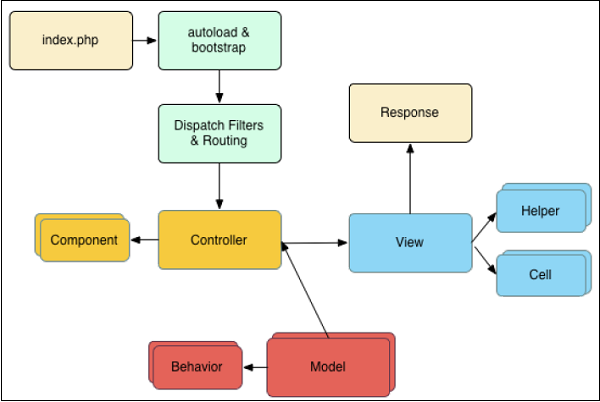
A typical CakePHP request cycle starts with a user requesting a page or resource in your application. At a high level, each request goes through the following steps −
- The webserver rewrite rules direct the request to webroot/index.php.
- Your application’s autoloader and bootstrap files are executed.
- Any dispatch filters that are configured can handle the request, and optionally generate a response.
- The dispatcher selects the appropriate controller & action based on routing rules.
- The controller’s action is called and the controller interacts with the required Models and Components.
- The controller delegates response creation to the View to generate the output resulting from the model data.
- The view uses Helpers and Cells to generate the response body and headers.
- The response is sent back to the client.
Comments
Post a Comment